
CSULB Projects
Ethical Hacking
Ethical Hacking

Risk Analysis
Total Risk | High Severity | High Probability | Low Fix effort |
https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:H/PR:L/UI:R/S:U/C:H/I:H/A:H/E:P/RL:O/RC:C/CR:H/IR:H/AR:H/MAV:N/MAC:L/MPR:L/MUI:R/MS:U/MC:H/MI:H/MA:H
Vulnerability Description
Remote Access to this valuable asset can be achieved and with this unauthorized access the attacker can escalate privileges in order to gain root access which can lead to data access and manipulation.
Lab Objective
The project’s objective is for learners to understand the importance of documentation and using skills acquired during the course to solve a challenge. Additionally, there are multiple ways of achieving the same goal when it comes to hacking.
Cracking Files
In this task, you are to crack the password that protects the file CrackMeIfYouCan.rar and document the process of your findings. Note: Documentation is extremely important when it comes to pentesting.
Using Hashcat only took 3 seconds :)
To complete this step do the following on the host OS in this case it's Windows 10 Pro
Extract the zip file with:
unzip CrackMeIfYouCan.zipNow we have the rar file we can use john to see the hash value with the following:
rar2john CrackMeIfYouCan.rar > Hash.txtWith the above text file now we move it over to Host machine for GPU cracking set it in the Hashcat directory
Open file with notepad++ to remove the CrackMeIfYouCan.rar: from the beginning of line and save
Open Powershell as Admin and run the following:
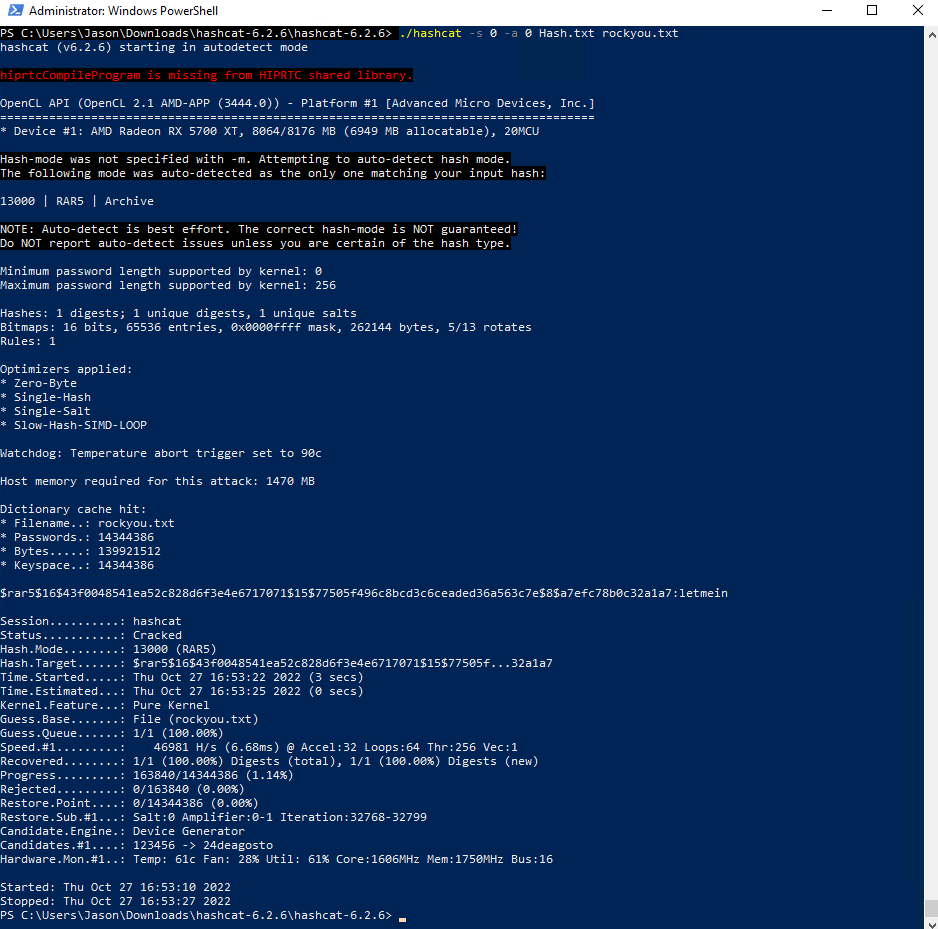
./hashcat -s 0 -a 0 Hash.txt rockyou.txtThis will perform the dictionary attack and get us the password to the file:
letmeinBelow is the result of the Hashcat output, we can see the hash is cracked:
Using 7-Zip to extract the files with the cracked password we can get the .rar file contents:

File Investigation
We can see there is a web page with a text file that has multiple lines of hashes that have been extracted:
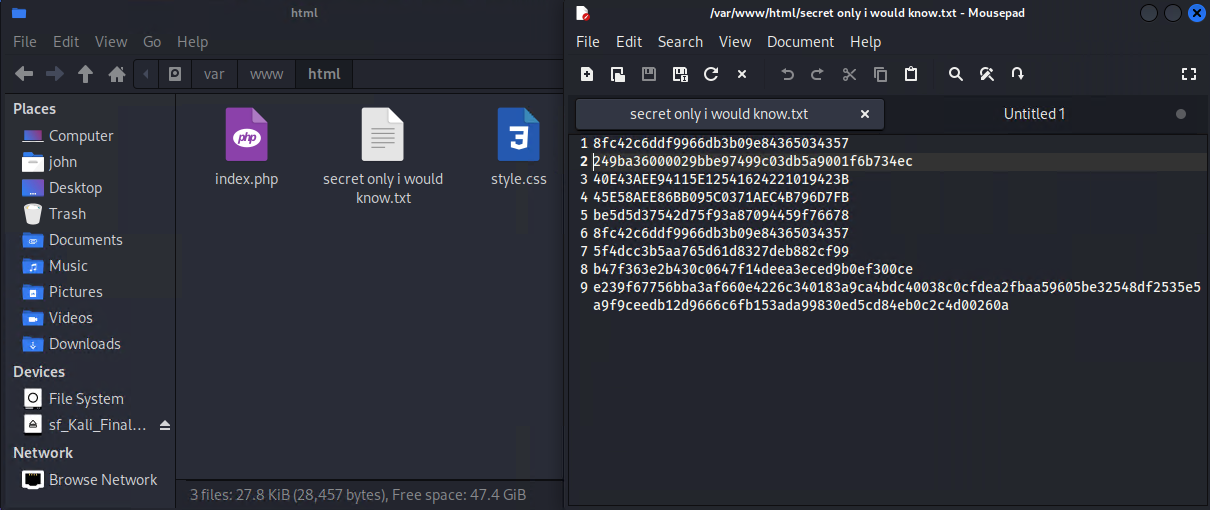
Since we now have a handful of hashes instead of using local resources we can speed up the process using an online web site like hashes.com to crack all the hashes at once, what a time saver.
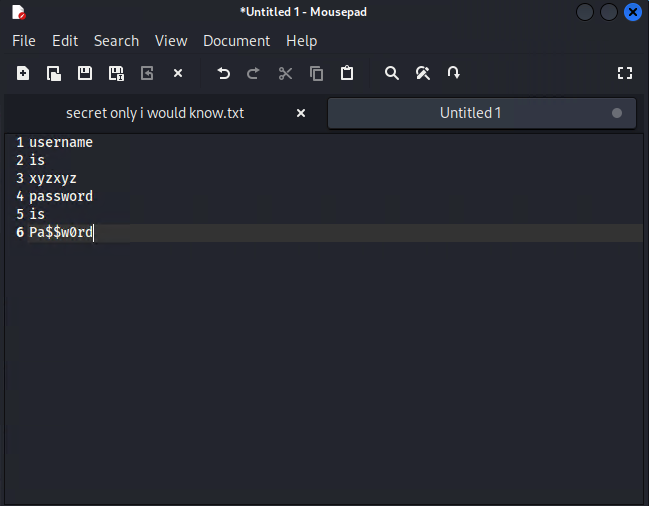
Now that we have the login credentials we can host the web page locally by using Apache
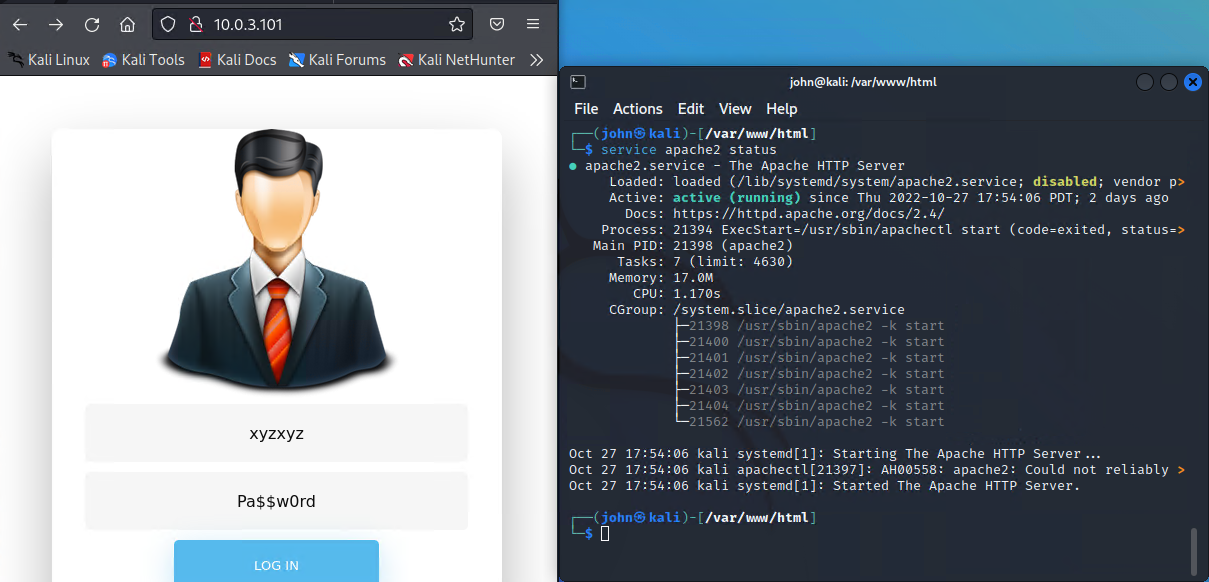

We can see that there is more to be uncovered
Vulnerability ScanningWith the netdiscover command we can see the Metasploitable VM’s IP on the network.
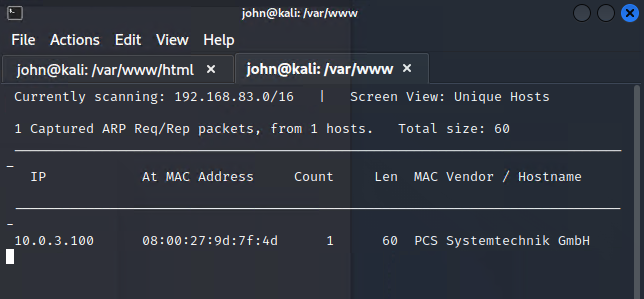
Now to enumerate the PC we can start with seeing what ports are open using Nmap
 Privilege Escalation
Privilege Escalation
We basically have multiple attack vectors to take. We will be picking Samba for this lab, we can use Metasploit Framework by launching the msfconsole. Using the multi/samba/usermap_script setting the RHOSTS to the IP of the Metasploitable VM we got earlier to 10.0.3.100 and launching the attack gets us a shell. After getting said shell we run the whoami command to see we are root

Now that we are logged in as root let’s check out the /etc/shadow file with:
cat /etc/shadow
 Ethical Hacking Final Project
Ethical Hacking Final Project